Near 10 months later my blog post about the ability of Microsoft Cloud to accelerate the GDPR compliance – part 2 where I launched it, and after several customers meetings that helped me to optimize it, now I believe it’s time to share again my view of the real Cloud Security and Compliance model.
What is it, and why did I build it?
Simply to tell, I realized the urgent need to help customers to understand how to manage end-to-end Security (and Compliance) in a new IT world that is rapidly shifting from classic on-premise solutions towards the adoption of Cloud computing. Customers are disoriented and they don’t have really clear where some Security controls are in charge of the Cloud Service Provider (CSP), where they still own these controls, and where the boundary is in this shared responsibility model. The business stakeholders realize the huge value of cloud computing and its benefits to accelerate the digital transformation in their organizations, but the Security and Compliance teams are worried by the lack of control that the Cloud paradigm seems to bring along those benefits.
This is why I started by adapting the well known NIST framework to highlight my first consideration, see the image below:
The IT service operations shift from on-premise to the different cloud delivery models (IaaS, PaaS, SaaS) can be interpreted as the 1st cloud security level, where the responsibility shift towards the CSP is also about Security & Compliance duties.
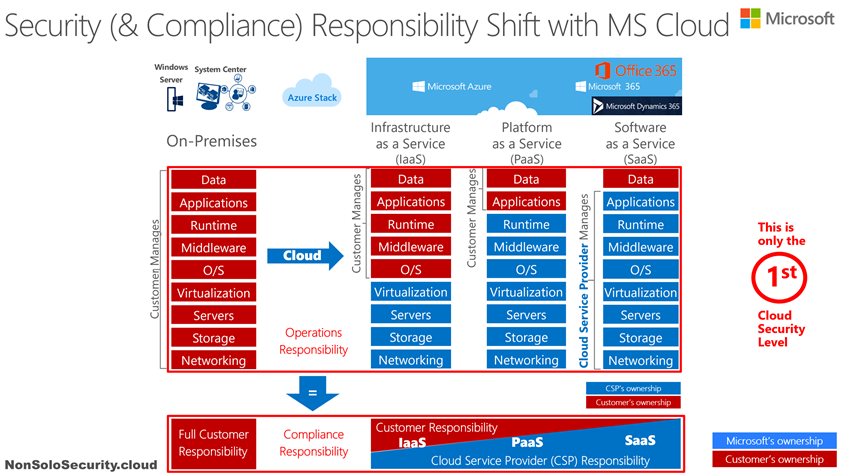
This first consideration can help to understand one of the reasons behind the statement you may have heard (especially from me :-), if you had this chance ;-)) of “Cloud as an accelerator of the customer’s security and compliance efforts”: the choice of cloud solutions, and more of the SaaS ones, can be a sort of “insurance” that shifts part of the responsibilities over the CSP. Moreover the layers in charge of the CSP’s responsibilities must also be covered by a contractual commitment, as required by the GDPR, when these solutions can process personal data.
In light of the GDPR requirement the Cloud must be compliant! (since it represents an external data processing)
Please note the bold text above: the end-to-end security and compliance requirements don’t end here, this is only the 1st level where you need and have to consider security controls (also in front of the GDPR law when it applies, of in front of any compliance requirements).
In order to give you the complete Cloud Security and Compliance model I’ve built the following diagram over time:
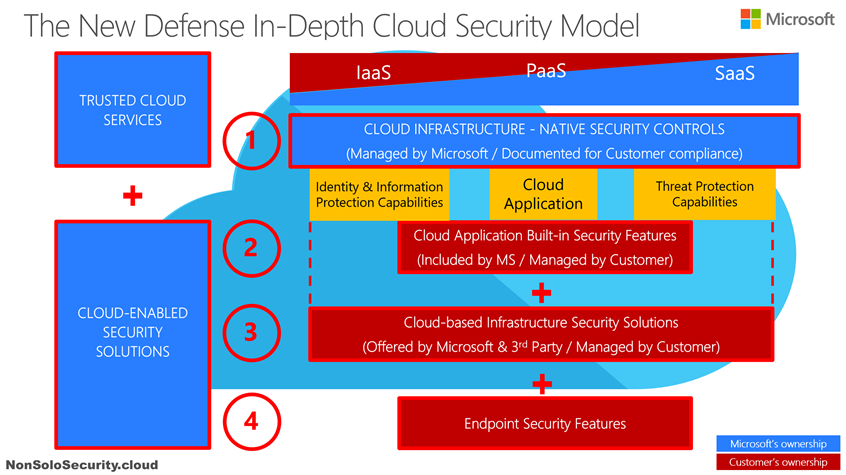
In addition to the 1st level, now you can see I added 3 more levels to understand how many layers you need to put security controls on, if you really need to secure the end-to-end interaction from a generic endpoint (a PC, tablet, smartphone, even an IoT endpoint) to a generic cloud application and to protect the data exchanged between them.
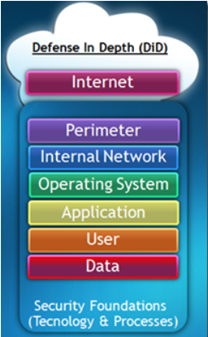
You need to apply security controls at every layer if you want to exercise the always valid principle of Defense In-Depth (as I’m sharing with you since the start of this blog in the late 2007)!!
As suggested by the color of those boxes, you can’t deem your CSP as totally responsible of the security & compliance requisites when you choose to use a cloud application, because there are 3 layers of controls that are still on your duty and responsibility to evaluate, adopt and manage!
Please note that while I mention Microsoft in the above diagram, this model is totally vendor-agnostic and it should be proposed by every (honest ;-)) CSP.
What’s the difference between the Microsoft Cloud and the rest of the market?
All the several CSPs in the market today, choose the name you want (Amazon, Google, Salesforce, and so on), must give you assurance of their commitments related to the 1st layer of this model, but they are unable to give you help with a cohesive and integrated set of security and compliance solutions at the remaining layers 2, 3 and 4: it’s up to you to find the best way to fill these layers with several 3rd party solutions from different vendors that leave gaps and expose this non-connected surface to possible attacks. As already recognized in the Security market and by forward-looking CISOs, this plethora of not homogeneous solutions are really impossible to manage and not effective in detecting advanced threats.
As of today, only Microsoft is powered with the ability to offer you a cohesive and integrated set of security and compliance solutions at all the 4 layers described above, and I’ll show you how… in the next blog posts , stay tuned!
Ciao
Feliciano